Imagine the blockchain world as a vast archipelago. Each island represents a unique blockchain network. While rich in resources, these islands often stand isolated. Cross-chain bridges like magical pathways connect islands and allow treasures to flow freely between them.
However, these bridges have weak spots. Pirates (malicious actors) have already exploited some weaknesses, not only stealing assets but undermining the bridges’ credibility.
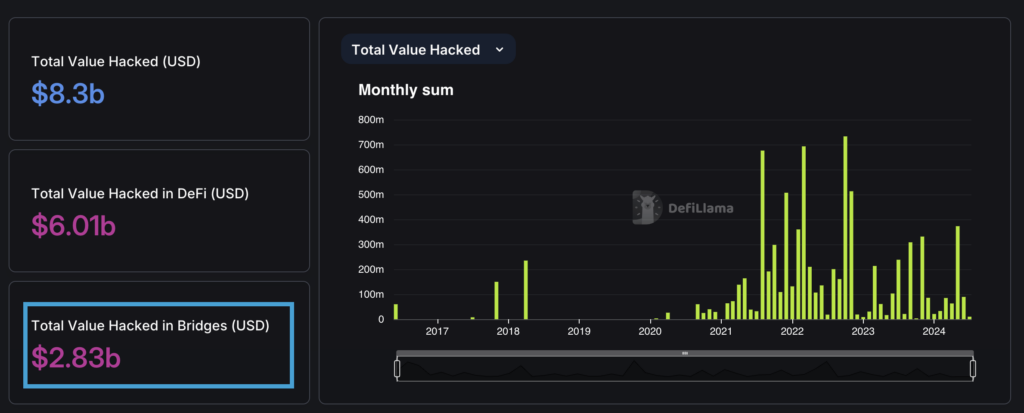
DefiLlama reports over $2.83 billion lost to cross-chain bridge hacks. Understanding vulnerabilities is your first line of defense.
This post will explore essential bridge security best practices. We stress the importance of DYOR (Do Your Own Research) – understanding the strengths and risks of your actions.
We’ll cover many aspects of bridge security and provide a comprehensive map to safely cross our connected blockchain islands.
How Do Cross-Chain Bridges Work?
Cross-chain bridges use two main methods to transport digital assets:
- The Gift Wrapping Method (Asset Wrapping):
- Your original asset is held in a secure vault on the departure island.
- A perfectly wrapped copy is created on your destination island.
- When you return, you unwrap your asset and reclaim the original.
The downside? This method often relies on a central authority to manage the wrapping.
- The Trading Post Method (Liquidity Pooling):
- You deposit your assets into a pool on your home island.
- An equivalent amount is released from a pool on your destination island.
This method is less centralized but can be affected by market fluctuations.
Types of Crypto Bridges You Might Encounter
In our blockchain archipelago, various types of bridges have emerged to connect different island networks. Let’s explore the most common and reliable bridge types currently in operation.
- Sidechain Bridges: Think of these as private ferries running alongside main shipping routes. They’re efficient but rely on a two-way system that could be targeted by pirates.
- Hashlock Bridges: These use cryptographic lockboxes to secure your assets during transit. Very secure, but potentially slower and more expensive.
- Plasma Bridges: These bundle multiple transactions together, like a ferry carrying several passengers at once. Faster, but might sacrifice some decentralization.
- Trusted Bridges: Centralized services, often with an oracle as the captain. Straightforward, but have been vulnerable to attacks in the past.
- Trustless Bridges: Decentralized fleets that don’t rely on a single trusted party. More secure but also more complex.
As you navigate the blockchain archipelago, remember that each bridge type offers unique advantages and challenges. Understanding this will help you make informed decisions in your cross-chain journeys.
Watch Out for Rough Seas: Common Cross-Chain Bridge Vulnerabilities
As you navigate these inter-island routes, be aware of potential dangers:
- Smart Contract Exploits: Even the best-designed bridges can have hidden flaws in their blueprints (code). Hackers, like skilled saboteurs, are constantly searching for weak points. A single overlooked detail could lead to a catastrophic breach.
- Compromised Keys: Private keys are like the captain’s secret logbook. If these fall into the wrong hands, it’s akin to pirates obtaining the captain’s log. The Harmony Horizon bridge incident of June 2022 is a stark reminder – $100 million was lost when attackers gained control of just two out of five required keys.
- Validator Exploits: Validator nodes are the lighthouse keepers of our blockchain archipelago. If these trusted sentinels are compromised, they might signal safe passage for malicious transactions. The risk amplifies when bridges rely on external validators.
- Centralization Risks: Some bridges opt for a centralized structure, like having a single port authority overseeing all inter-island travel. While this can streamline operations, it creates a single point of failure. If compromised, the entire network of bridges could be at risk.
- Oracle Manipulation: Oracles are like the weather stations of our blockchain archipelago. Centralized oracles can be as vulnerable as a single weather station giving faulty readings. Decentralized oracles, on the other hand, are like a network of weather flow marks spread across the sea, each contributing data to form a more reliable consensus.
What are the roots of these weak spots? The vulnerability of these bridges often stems from two main factors:
- Reliance on oracles: They provide crucial information to guide the bridges. However, if an oracle is compromised, it can lead ships (or in our case, assets) astray.
- Lack of regulations: There’s no unified coast guard patrolling these waters, making it easier for bad actors to operate.
Staying Safe on Your Journey: Best Practices of Using Cross-chain Bridges
While bridge operators are responsible for building secure passages, it’s you who play a crucial role in your own safety. Here’s your traveler’s guide to navigating cross-chain bridges:
- Verify Your Port of Call: Before boarding any ferry (bridge), double-check that you’re at the correct dock. Scammers often set up convincing-looking, but fraudulent, boarding areas. Always verify URLs and link sources to ensure you’re using the legitimate bridge, not a deceptive imitation.
- Choose Transparent Operators: Opt for ferry services (bridges) that regularly invite independent inspectors to examine their vessels and operations. The most reputable bridges often host “bug hunts” – think of these as public safety drills that boost security and demonstrate their commitment to passenger safety.
- Stay Informed: Keep your ear to the maritime radio. Stay updated on bridge announcements, security alerts, and best practices for safe passage. Knowledge is your life vest in these waters.
- Double-Check Your Cargo Manifest: Before your assets set sail, carefully review all transaction details. This final check is your last line of defense against errors or potential scams.
- Use Reputable Services: Stick to well-known and audited bridges. While newer routes might offer exciting possibilities, they may not have weathered many storms yet.